This work package has the following main objective:
Define mathematical methodologies for Situational Awareness applied to interdependent critical infrastructures.
The main activities performed by this Work Package are:
TASK 301: Data Fusion Models for Situational Awareness in interdependent CIs
Data fusion techniques has be extended to include interdependencies as a source of information able to discriminate among several possible interpretations of measured events. Using distributed Dempster-Shafer based inference models, it has been possible to include some observations coming from different sources and use them in an interdependency model to propagate risk along several infrastructures.
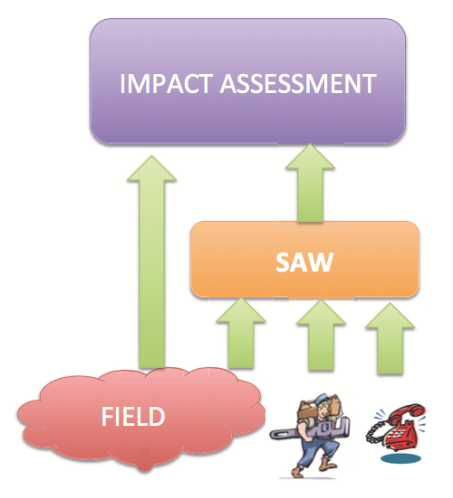
To achieve such a result a Situation Awareness (SAW) module has been interposed between the field and the interdependency model.
Such a SAW layer is fed with the fields data, as well as with other information coming from different sources, such as customer or maintenance/recovery teams’ reports (i.e., unnoticed malfunctioning or blackout) and government or civil protection information (e.g., a tsunami warning). Such a use of SAW leads to an augmented impact assessment in which domino effects can be exploited, with their respective confidence levels. This implies also that the impact assessment should be done with a tool able to manage uncertainty.
TASK 302: Complex Event Processing Models
Complex Event Programming (CEP) models and management SW are focused on assessing the evolution of a specific situation on the base of signals coming from sensors or communication sources. The higher the complexity of a scenario, in terms of number and hierarchy levels of concatenated events, the higher is the difficulty in modeling all the main possible paths that the situation can evolve into.
CEP has been used to analyse different sequences of events at local and geographic level. The local application is dedicated to the analysis of the sequence of events that can happen into a commuting station for the telecommunication infrastructure: readings coming from different sensors have been put in temporal relation to produce the right alarms and to discriminate from false positive.
At geographical level, Complex Event Programming has been used to analyse the behaviour of gas distribution in presence faults on the transmission pipes and considering some storage facilities.
TASK 303: Game Theoretical Models
Protecting critical infrastructures against intentional attacks is fundamentally different from protecting against random accidents or acts of nature. Intelligent and adaptable adversaries may try different offensive strategies or adapt their tactics in order to bypass or circumvent protective security measures and exploit any remaining weaknesses. Approaches that attempt to directly assess probabilities for the actions of intelligent antagonists, without modelling how they depend on the defender’s choices (which in turn may depend on assumptions about attack probabilities), are liable to produce ambiguous and/or mistaken risk estimates that are not suitable for guiding resource allocations in practice.
Instead of designing a defence against a specific attack, in this Task Game Theory has been used to design a defence against a sophisticated attacker who plans in anticipation. Furthermore, Game Theory has been used to model trust, incentives, and externalities that arise in security systems.
The Task developed the attack-defence game model providing a quantitative methodology for risk assessment and focusing on the quantification of probability of occurrence for interdependent critical infrastructures. Within every single critical infrastructure, it has been supposed to have an Intrusion Detection System (IDS) with its own detection capability (a priori known). In order to visualize the results, and simulate the developed model, a graphical user interface was designed integrating the following functionalities: Selection of the game mode; Visualization of infrastructure network and interdependencies; Simulation of the game; Visualization of results.
TASK 304: Digraph-based models
Development of digraph-based model of information and control flow in interdependent networks and study of efficient algorithms for the recovery of such structures in the event of disruptions to graph topology.
The objective of the model developed in this task is to reproduce the normal behaviour of a gas distribution system describing the interdependencies between the main components in the system and, at the same time, highlight the vulnerabilities of the gas supply network. A method to identify the vulnerabilities based on a linear programming approach has also been provided.
To preserve the functionality of the pipeline network, the proposed model provides information about the most vulnerable side of the network identifying its critical components. Such components are identified resolving an optimization problem. In the real network, the malicious control of the corresponding MR stations implies the degradation of the gas supply network. The objective, looking at the problem from the attacker point of view, is to disconnect the graph associated to the pipeline. In the real network, the objective of this approach is to identify isolated areas without gas supply